Recently having installed SCUP and set it up to publish updates using an internal CA I needed to deploy the custom certificate to all the client machines so that they will receive and install the updates correctly. It turns out that the place to install a “Trusted publisher” certificate is not where you would think.
- Open “Group Policy Manager”
- Under Computer Configuration – Windows Settings – Security Settings – Software Restriction Policies
- Right click and create a new SR policy if you haven’t got one already
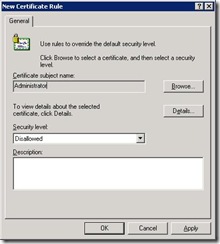
- Under Additional rules right click and create new “Certificate rule”
- Click browse and select the exported certificate that is being used to sign the updates (.cer file)
- Change the “Security Level” to Unrestricted otherwise you will stop the computers running any programs!
- Exit out of the windows and that should be all.
Update 1 29/01/2013 – on Server 2012 / 2008 R2 you might get an additional dialogue:
Choose “No” as you don’t want to enforce the rules, just push the certificate out to client machines.
I should also point out that this article was written in 2008 using Server 2003 and I haven’t checked if there is a newer / better way to push out a certificate in newer versions of Windows…
Update 2 – Turns out in newer Group Policy you can deploy the certificate direct to the “Trusted publisher” certificate container see here.
Remember that if you are using a self signed certificate you need to push your stand-alone root into “Trusted Root Certificate Authorities” as well. I’ve not tested if this method works with down level clients like Windows XP
[tags]scup,group policy[/tags]











Excellent, thanks.
Thanks. I looked for 2 -3 days to find this information and your site is the only place I could find this information. Every other place basically states that you can’t add Trusted Publishers through GPO’s.
I needed to deploy a Office Word 2007 add-in as a MSI. The security requirements are the same as for ClickOnce deployment, and this requires that the manifest is signed.
Office Word 2007 has rather over-ambitious policy in that it will ask the user for confirmation even if the manifest is signed by a trusted certificate – the certificate must also be a trusted publisher.
The available documentation from Microsoft is just plain wrong/applies to a different version (it appears this has changed in 2008), as is most recommendations on the Internet, where it’s said that a certificate trust list needs to be created. Won’t help in this scenario.
But your description does the trick!
I tried reading the Microsoft documentation again, knowing what I now know with your help, but I still can’t really see how I would be able to figure out the connection between software restriction policies and the Trusted Publishers certificate category on the target workstations.
Thank You!
Thank you! Why the hell Microsoft do not tell you this I have no idea…
Thanks! After reading all those wonderful microsoft articles I finally found someone who knew what they were talking about!
For Windows 2003 I agree that “Software Restriction Policy” was the only way to perform the certificate deployment.
But since Windows 2008 there is a more simpler and less risky way.
Just import your certificate into “Trusted Publishers” section of the GPO. MS documentation is here:
http://technet.microsoft.com/en-us/library/cc770315(WS.10).aspx
Cheers,
Patrick
Thank you…
I’ve been reading through a shitload of Microsoft documentation for the past 3 days trying to find out how to fix this !
#Fail
Nice. Thanks for posting this. It helped me out, it was exactly what I was trying to do.
Bruce
Hi,
got a problem and i don’t understand where is the issue.
I am using sonicwall security appliance – firewall etc.
I am using this device also so i can filter out what users can go from my AD group on the internet, they need to login on a interface using their username and password but the certificate is self signed and manually it can be imported on each computer but i want to use gpo to deploy the certificate on my computers i had inserted in this way and it is not working http://technet.microsoft.com/en-us/library/cc770315(WS.10).aspx
If i run the gpresult command on it says that is applied on the current machine (tried on winxp)
I would need help where is the mistake….
Thanks in advance
Ervin
When following this there were addtional dialogues that appeard that you fail to add in the shot. It prompts to say – A certificate already exists for this rule, replace? After that another box appears asking how the rule is to be applied. Please update your documentation regarding this.
It would appear that you still have failed to update your documentation regarding additional dialogues. Leave any of the settings as default? What?
Hello Chuck,
I’ve had a look back at this post and am still happy with the content and that it stands up. I have re-created the set-up on a 2012 server and added the additional dialogue box that now appears. I suspect that you get a warning about a certificate or rule already existing as your not starting with a blank GPO and that you have something already in-place. Have you tried the better way of adding certificates via GPO that are no available in 2008 R2 / 2012?
This post was published back when 2003 and XP were the standard operating systems.
Ben.